SAP Fiori: How to Quickly Search for Startable Applications in a Particular Role
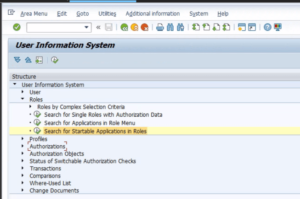
In the ever-evolving landscape of SAP administration, efficiently managing user access to various applications is a critical task. One powerful tool at the disposal of SAP administrators is the “Search for Startable Applications in Roles” function within SUIM (SAP User